What Is Mobile Device Management? Role in Endpoint Security and Benefits
Heimadal Security
JULY 25, 2023
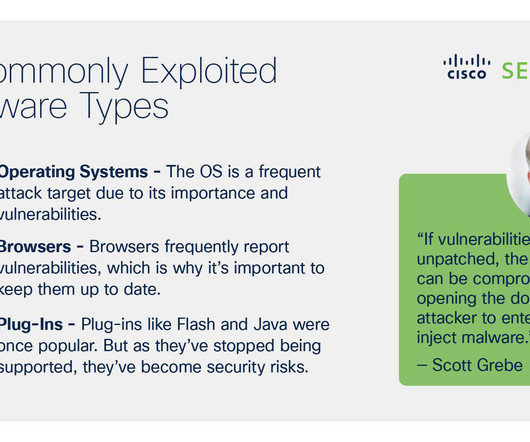
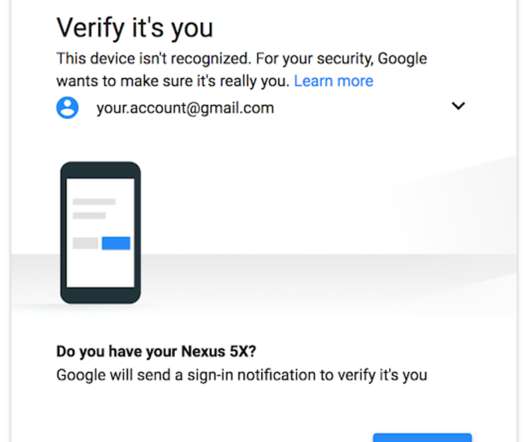
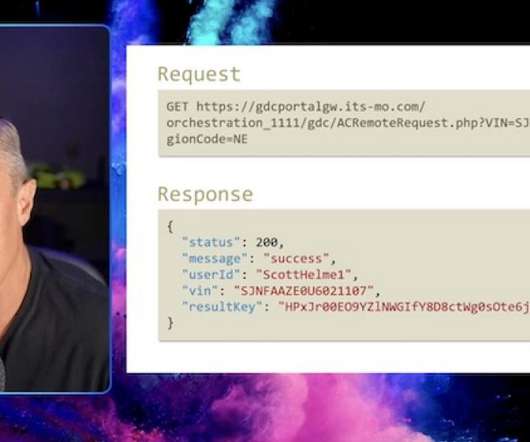
Mobile device management (MDM) is software that enables IT teams to supervise and secure all mobile endpoints in a company`s digital perimeter: laptops, tablets, smartphones, etc. By using a Mobile Device Management solution, IT administrators can track […] The post What Is Mobile Device Management?















































Let's personalize your content