Internet Backbone Giant Lumen Shuns.RU
Krebs on Security
MARCH 8, 2022
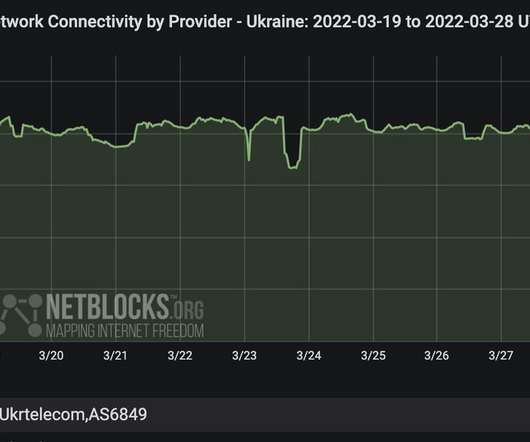
Lumen Technologies , an American company that operates one of the largest Internet backbones and carries a significant percentage of the world’s Internet traffic, said today it will stop routing traffic for organizations based in Russia. ru) from the Internet. More information can help, even as disinformation circulates.










































Let's personalize your content