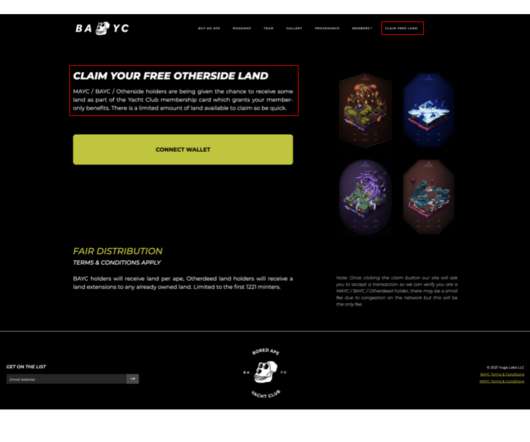
Hackers stole over $250,000 in Ethereum from Bored Ape Yacht Club
Security Affairs
JUNE 5, 2022
Hackers have stolen over $250,000 in Ethereum from Bored Ape Yacht Club (BAYC), this is the third security breach it suffered this year. ” reads the analysis published by blockchain cybersecurity firm CertiK. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g.










































Let's personalize your content