Ransomware gangs are exploiting CVE-2022-26134 RCE in Atlassian Confluence servers
Security Affairs
JUNE 12, 2022
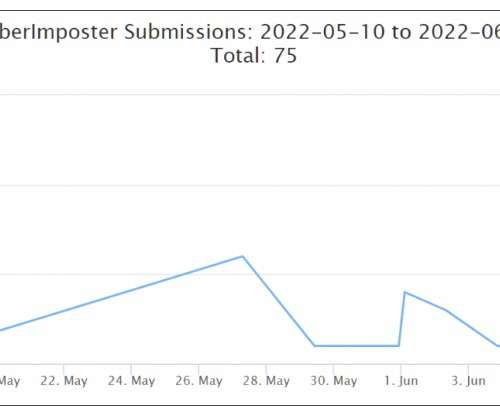
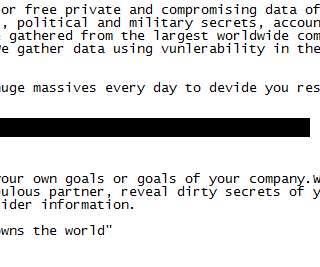
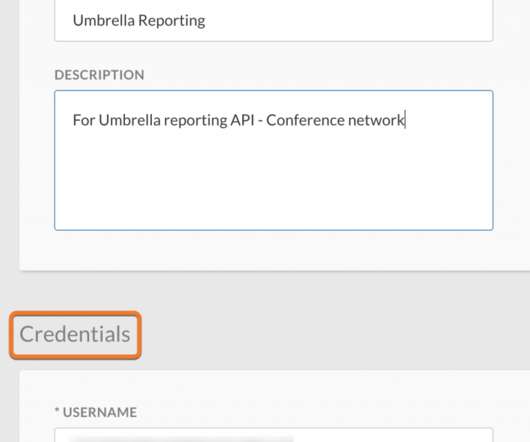
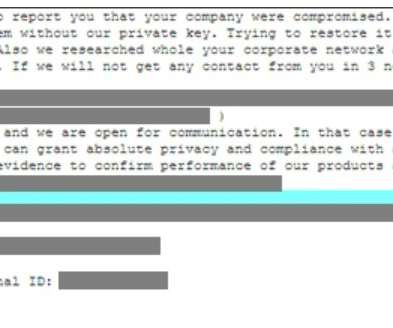
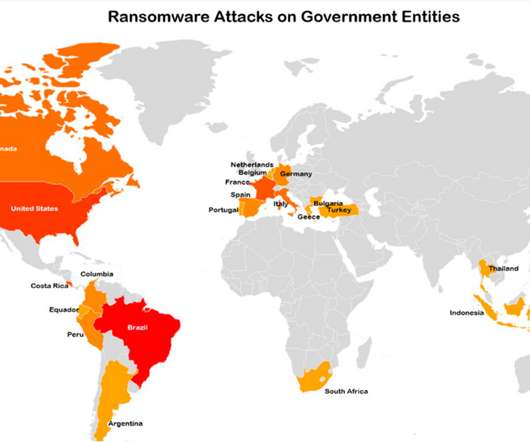
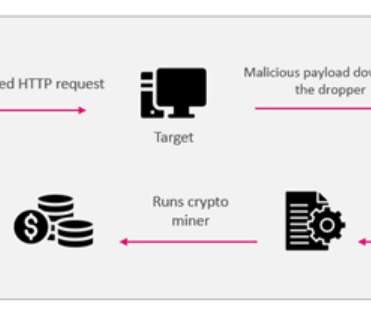
Ransomware gangs are actively exploiting CVE-2022-26134 remote code execution (RCE) flaw in Atlassian Confluence Server and Data Center. Multiple ransomware groups are actively exploiting the recently disclosed remote code execution (RCE) vulnerability, tracked as CVE-2022-26134 , affecting Atlassian Confluence Server and Data Center.



































Let's personalize your content