What Are DNS Records? Types and Role in DNS Attacks Mitigation
Heimadal Security
FEBRUARY 23, 2023
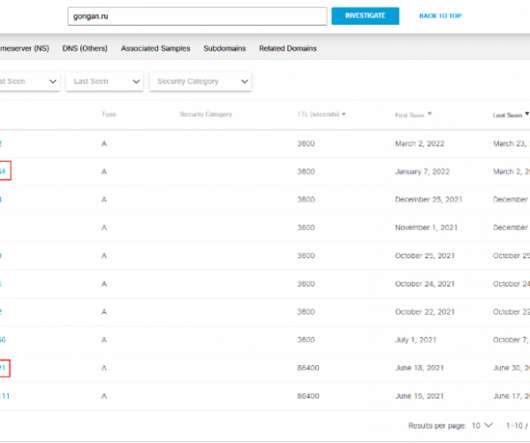
DNS records or resource records (RR) contain various types of data about domain names and IP addresses. They are stocked in DNS databases on authoritative DNS servers. DNS records offer information about what IP address is associated with what domain, for example.










































Let's personalize your content