Users in Italy and Kazakhstan Targeted by Spyware Provider
Heimadal Security
JUNE 24, 2022
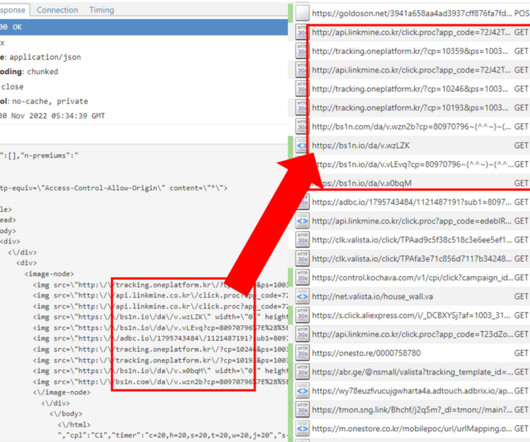
Every campaign that TAG was made aware of began with […]. The post Users in Italy and Kazakhstan Targeted by Spyware Provider appeared first on Heimdal Security Blog. What Happened?















































Let's personalize your content