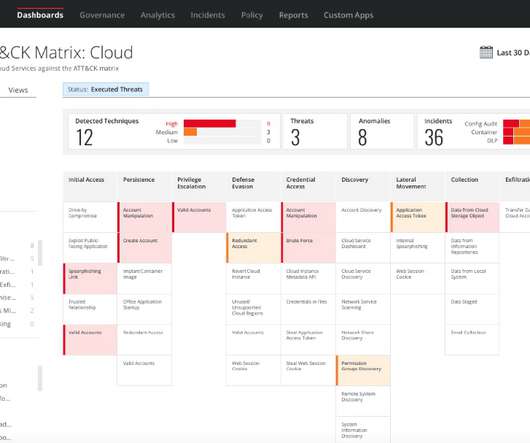
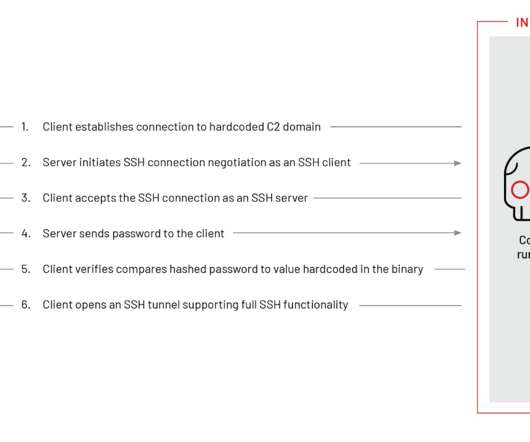
Cyber Threat Hunting Techniques & Methodologies
Heimadal Security
MAY 8, 2023
The only way to stay safe while doing some online surfing is to buy or try out a cybersecurity product: antivirus, antimalware, email security suits, […] The post Cyber Threat Hunting Techniques & Methodologies appeared first on Heimdal Security Blog.














































Let's personalize your content