How Machine Learning Can Accelerate and Improve the Accuracy of Sensitive Data Classification
Thales Cloud Protection & Licensing
DECEMBER 11, 2023
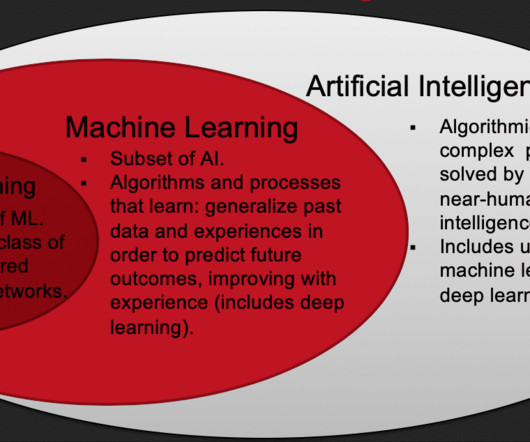
As organizations create more diverse and more user-focused data products and services, there is a growing need for Machine Learning (ML) to automate classification and improve the accuracy of results. Traditional approaches to data classification use manual tagging which is labor-intensive, error-prone, and not easily scalable.












































Let's personalize your content